Stack canaries: overestimating software protection
Android, Windows, Mac, Linux… All operating systems contain stack canaries — one of the most common forms of software protection. These safeguards that protect computer systems from intrusions are perceived as very effective. Yet, recent research carried out by EURECOM and the Technical University of Munich show that most stack canaries contain vulnerabilities. The results obtained through a project led by the German-French Academy for the Industry of the Future highlight the fragility of computer systems in the context of increasingly digitized organizations.
During the 19th century, canaries were used in coal mines to forewarn of impending firedamp explosions. The flammable, odorless gas released by the miners’ activities caused the birds either to lose consciousness or to die. This alerted the workers that something was wrong. Several decades later, in the early 2000s, researchers in cybersecurity were inspired by the story of canaries in coal mines. They invented a simple protection system for detecting software corruption—calling it “stack canary”. Since then, it has become one of the most common protection systems in the software we use and is now present in almost all operating systems. But is it really effective?
Perhaps it seems strange to be asking this question over 20 years after the first stack canaries were used in computer products. “The community assumed that the protection worked,” explains Aurélien Francillon, a researcher in cybersecurity at EURECOM. “There was some research revealing potential vulnerabilities of stack canaries, but without any in-depth investigation into the issue.” Researchers from EURECOM and the Technical University of Munich (TUM) have therefore partnered together to remedy this lack of knowledge. They assessed the vulnerabilities of stack canaries in 17 different combinations of 6 operating systems, to detect potential defects and determine good practices to adopt to remedy the situations. Linux, Windows 10, macOS Sierra and Android 7.0 were all included in the studies.
“We showed that, in the majority of operating systems, these countermeasures for detecting defects are not very secure,” Aurélien Francillon explains. 8 out of the 17 tested combinations are qualified by the researchers as using an inefficient stack canary (see table below). 6 others can be improved, and the last 3 are blameless. This study of the vulnerabilities of stack canaries, carried out in the context of the Secure connected industry of the future (SeCIF) project, part of the German-French Academy for the Industry of the Future, is linked to the growing digital component of organizations. Industries and companies are increasingly reliant on connected objects and IT processes. Defects in the protection devices for operating systems can therefore endanger companies’ overall security, whether it be access to confidential data or gaining control of industrial machinery.
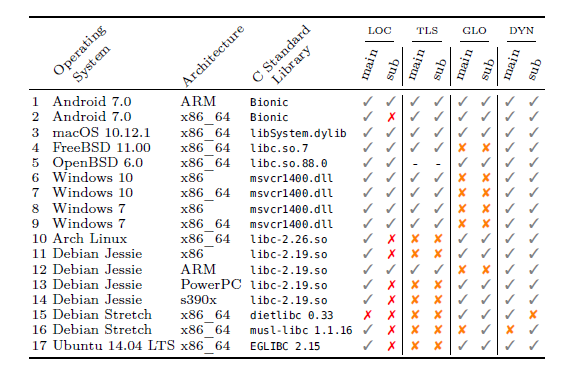
Out of the 17 operating systems tested, only Android 7.0 “Nougat”, macOS 10.12.1 “Sierra”, and OpenBSD 6.0 (Unix) had completely secure stack canaries. A red cross means that it is possible to bypass the stack canary in the given combination. An orange cross mean that stack canary security can be improved. Table columns are different memory types from a programming logic standpoint.
The canary in the memory
To understand the impacts of the defects revealed by this research, it is important to first understand why stack canaries are used and how they work. Many attacks that occur are aimed at changing values in a program that are not meant to be changed. The values are stored in memory space. “Let’s say this space has a capacity of 20 bytes,” says Julian Kirsch, a cybersecurity researcher at TUM and co-author of this study. “I would store my name and height on 20 of these bytes. Then, on another space located just behind it, I would store my bank account number. If a hacker wants to corrupt this information, he will add values, for example by adding a number to the value for my height. By doing this, my height data will overflow from the 20-byte space to the space where my bank account number is stored, and the information will no longer be correct. When the program needs to read and use this data, things will go wrong.”
In more complex cases for operating systems, the consequences include more critical errors than the wrong bank account number. To determine whether the information stored in the memory was altered, a known numerical value can be inserted between the storage spaces, as a type of memory buffer. If a hacker adds information, like in Julian Kirsch’s example in which the height was changed, everything will shift, and the value indicated in the memory buffer will change. The stack canary is simply a memory buffer. If the stack canary’s security is compromised, the hacker can modify it and then hide it by resetting it to the initial value.
To make the hacker’s work more difficult, the value of most stack canaries is changed regularly. A copy of the new value is stored in another memory space and both values, the real one and the reference one, are compared to ensure the integrity of the software. In their work, the researchers showed that the vulnerabilities of stack canaries are primarily linked to the place where this reference value is stored. “Sometimes it is stored in a memory space located right next to the stack canary,” Julian Kirsch explains. The hacker therefore does not need to access another part of the system and can change both values at the same time. “This is a defect we see in Linux, for example, which really surprised us because this operating system is widely used,” the TUM researcher explains.
How can such commonly used protection systems be so vulnerable on operating systems like Linux and Windows? First of all, Aurélien Francillon reminds us that stack canaries are not the only countermeasures that exist for operating systems. “In general, these are not the only countermeasures used, but stack canaries still represent significant hurdles that hackers must overcome to gain control of the system,” the EURECOM researcher explains. Their vulnerability therefore does not threaten the entire security for operating systems, but it is one less door for hackers to break into.
The second, less technical reason for permissiveness regarding stack canaries is related to developers’ choices. “They do not want to increase the security of these countermeasures, because it would it decrease performance,” Julian Kirsch explains. For software publishers, security is a less competitive argument than the software’s performance. Greater security implies a greater allocation of computing resources for tasks that do not directly respond to the software user’s requests. Still, customers rarely appreciate computer system intrusions. Considering organizations’ growing concerns about cybersecurity issues, we can hope that the software chosen better integrates this aspect. Security could then become a serious argument in the software solution market.




Leave a Reply
Want to join the discussion?Feel free to contribute!