Using hardware to defend software against cyber-attacks
Software applications are vulnerable to remote attacks via the internet or local networks and are cyber-attackers’ target of choice. While methods combining hardware and software have already been integrated into the most recent processors to prevent cyber-attacks, solutions based solely on hardware, which by definition cannot be remotely attacked, could soon help defend our computer programs. Jean-Luc Danger, a researcher at Télécom ParisTech, works on these devices that are invulnerable to software attacks.
[divider style=”normal” top=”20″ bottom=”20″]
This article is part of our series on Cybersecurity: new times, new challenges.
[divider style=”normal” top=”20″ bottom=”20″]
Nothing and no one is infallible, and software is no exception. In practice, it is very difficult to design a computer program without flaws. Software is therefore on the frontline of cyber-attacks. This is especially true since software attacks, unlike hardware attacks locally targeting computer hardware, can be carried out remotely using a USB port or internet network. These cyber-attacks can affect both individuals and companies. “Compared to software attacks, hardware attacks are much more difficult to carry out. They require the attacker to be in the vicinity of the targeted machine, and then to observe and disrupt its operation,” explains Jean-Luc Danger, a researcher in digital and electronic systems at Télécom ParisTech.
So what are the solutions for protecting software? “We intuitively know that if we design antivirus software to protect against software attacks, this protective software can itself be the victim of an attack,” says Jean-Luc Danger. Hardware protection devices, which cannot be remotely attacked, could therefore offer an effective solution for improving the cybersecurity of computer programs from the threat of software attacks.
Hybrid methods for countering attacks
Software, or a computer program, is a series of instructions performed sequentially. A program can therefore be presented as a graph, in which each node represents an instruction. This flowchart, or control flow graph, helps ensure that the series of nodes are correctly performed.
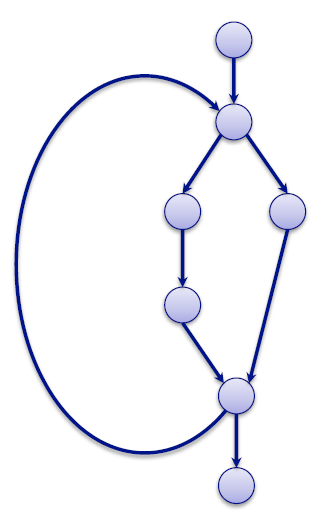
Each point symbolizes an instruction, and the arrows which connect them represent
the sequence for executing these instructions.
During a cyber-attack, the attacker identifies a flaw in order to inject code and integrate invalid instructions, or use the existing code to change the execution sequence of the instructions. The malicious code can for example allow the attacker to access the targeted system’s memory.
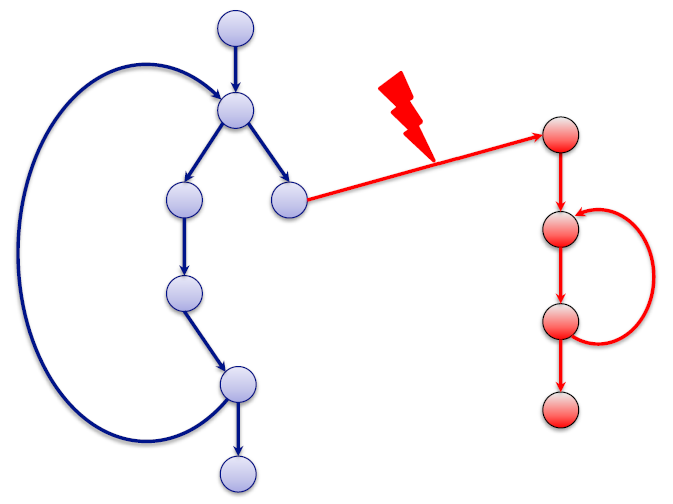
Here, a code injection attack, with the execution of an invalid series of instructions.
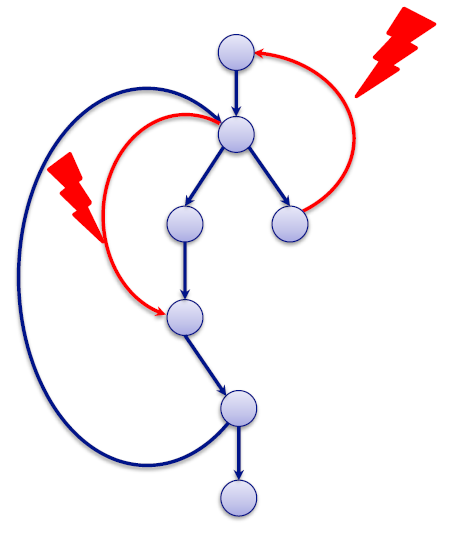
In the case of a code reinjection attack, the flow of the execution of tasks is altered.
“There are many different methods for protecting software: antiviruses, which detect infected programs, solutions for making the code unreadable, programs that check the integrity of the control flow graph…” Jean-Luc Danger explains. Some hybrid solutions, involving both hardware and software, are already integrated into current processors. For example, memory management units enable each program to have a dedicated memory range protected by a virtual address, which limits the damage in the event of a cyber-attack. In addition, processors can be equipped with a virtualization device on which a virtual machine can be installed with its own operating system. If the first system suffers a software attack, the virtual machine could take over.
Although these are hardware solutions, since they involve the processor being physically altered, they require a minimum amount of configuration and software writing in order to work, which makes them vulnerable to software attacks. However, hardware-only solutions are being developed to protect from cyber-attacks.
Stacks of memory “plates” and digital signatures
“There is already a fully hardware-based solution that will soon be integrated into Intel processors: shadow stacks. These stacks of hardware offer an interesting solution for preventing cyber-attacks targeting the sub-programs,” Jean-Luc Danger explains.
Within a program, an instruction can refer to another series of instructions, which then represents a sub-program. Once the sub-program has run, the data is sent back to the initial starting point to be reintegrated into the main program’s chain of instructions: this is the critical moment, when a cyber-attack can divert the data and send it to an abnormal instruction.
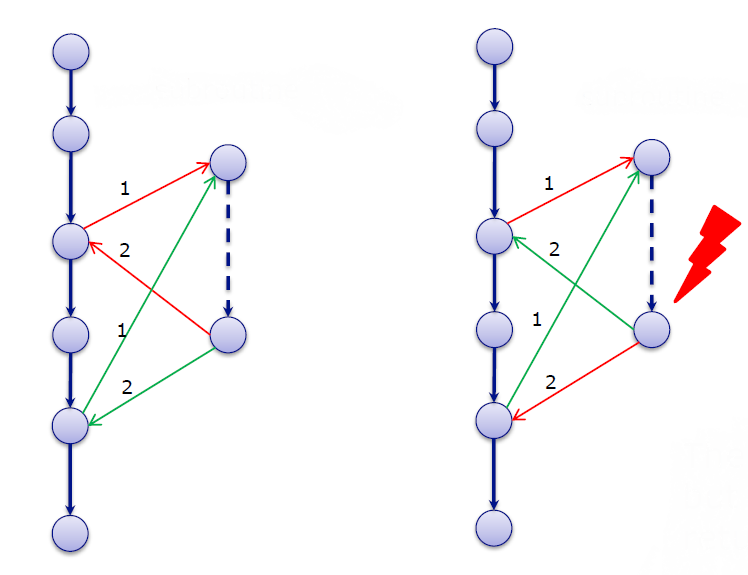
In the event that a sub-program is run
(here, the chain consists of two nodes, to the right of the main program),
the data can be sent back to the wrong instruction during a cyber-attack.
The shadow stack is intended to stop this type of attack. This “stack” mechanism, in which the memory is physically stored in the form of “stacked plates”, leaves a physical trail of the nodes travelling to and from the sub-program. “The node’s address is ‘stacked’ on the first ‘plate’ when the sub-program runs and is ‘unstacked’ once the operation is complete,” explains Jean-Luc Danger. It is therefore impossible to redirect the sub-program through a software attack, since the starting and ending points have been registered physically.
“At Télécom ParisTech we are working with the spin-off Secure-IC to develop HCODE, a fully hardware-based type of protection which complements shadow stacks and is relatively non-invasive in relation to microprocessors’ current structures,” explains Jean-Luc Danger. HCODE ensures that the jumps between the program and sub-program are integrated and associates a digital signature (or hash value) with each series of instructions in the program. Together, all the signatures and expected jumps form reference data or metadata, which is stored on the HCODE hardware model, added to the processor. By protecting the integrity of the jumps and series of instructions in this way, HCODE makes it possible to resist both software attacks and physical injection-of-fault attacks. If an error is injected into a series of instructions or a single instruction, an alarm will be triggered and will prevent the attack.
“The idea is that this hardware can be added to any type of processor, without changing the core,” Jean-Luc Danger explains. These hardware security measures are impossible to modify through a software attack and are also faster at detecting intrusions. So what are the next steps for the researcher, his team and secure-IC? “Validate the concept in several types of processors and refine it, reduce the memory required for storing the signatures, and then develop it on an industrial scale.” Perhaps this will allow our software to rest easy…
Also read on I’MTech Secure-IC: protecting electronic circuits aganinst physical attacks



Leave a Reply
Want to join the discussion?Feel free to contribute!