Octave: trustworthy and robust voice biometric authentication
Surely, voice biometric authentication would be an easier alternative to the large amount of passwords that we use daily. One of the barriers to exploitation involves robustness to spoofing and challenging acoustic scenarios. In order to improve the reliability of voice biometric authentication systems, Nicholas Evans and his team at Eurecom are involved since June 2015 — and for a two years duration — in a H2020 European project called Octave.
What is the purpose of the Objective Control of Talker Verification (Octave) project?
Nicholas Evans: The general idea behind this project is to get rid of the use of passwords. They are expensive in terms of maintenance: most people have many different passwords and often forget them. While simultaneously relieving end-users from the inconvenience of dealing with textual passwords, Octave will reduce the economic and practical burden of service providers related to password loss and recovery. Octave will deliver a scalable, trusted biometric authentication service — or TBAS. The project is about providing a reliable service that works in diverse, practical scenarios, including data-sensitive and mission-critical application.
Eurecom is leading the third work package of this H2020 European project. What is the role of the school?
NE: Our main mission is to ensure the reliability of the underlying automatic speaker verification technology. To do so, our work package has two objectives. First, insuring the proper functioning of the TBAS in a variety of environments. Indeed, the Octave platform should work properly whether it be deployed in a limited bandwidth and channel-variable telephony context or in a noisy physical access context. Eurecom’s focus is on our second objective, which is counter-spoofing.
How does your research team ensure the security of the system against spoofing?
NE: If I want to steal your identity, one strategy might be to learn a model of your voice and then to build a system to transform mine into yours. Anything like that would typically introduce a processing artefact. I could also try to synthetize your voice, but again this would produce processing artefacts. So, one of the highest level approaches to identify a spoofing attempt is to build an artefact detector. In order to do that, we apply pattern recognition and machine learning algorithms to learn the processing artefacts from huge databases of spoofed speech.

So researchers have a large database of spoofed speech at their disposal?
NE: This is a very tricky issue. Ideally, we would use real data, that is to say real examples of spoofed speech. These don’t exist, however. Even if they did, they would most likely not contain many samples. Therefore, we have to generate these spoofed speech datasets ourselves. We try to imagine how an attacker would try to spoof a system and then we fabricate a large number of spoofed samples in the same way. Fortunately, we can do this much better than a spoofer might, for we can imagine many possibilities and many advanced spoofing algorithms.
However, this methodology results in an unfortunate bias: when we use artificially generated datasets of spoofed speech, then we are in a really good position to know how spoofers faked the voice, because… well, we were the spoofers. To design reliable spoofing detectors we must then try to use the databases blindly, that is to say we must try not to use our knowledge of the spoofing attacks – in the real world, we will never know how the spoofing attacks were generated.
Luckily a very large, standard database of spoofed speech is now available and this database was used recently for a competitive evaluation. Since participants were not told anything about some of the spoofing attacks used to generate this database, the results are the best indication so far of how reliably we might be able to detect spoofing in the wild. Eurecom co-organised this evaluation, ASVspoof 2015, with another Octave partner, the University of Eastern Finland, among others.
Who are the other partners working along Eurecom on the Octave project?
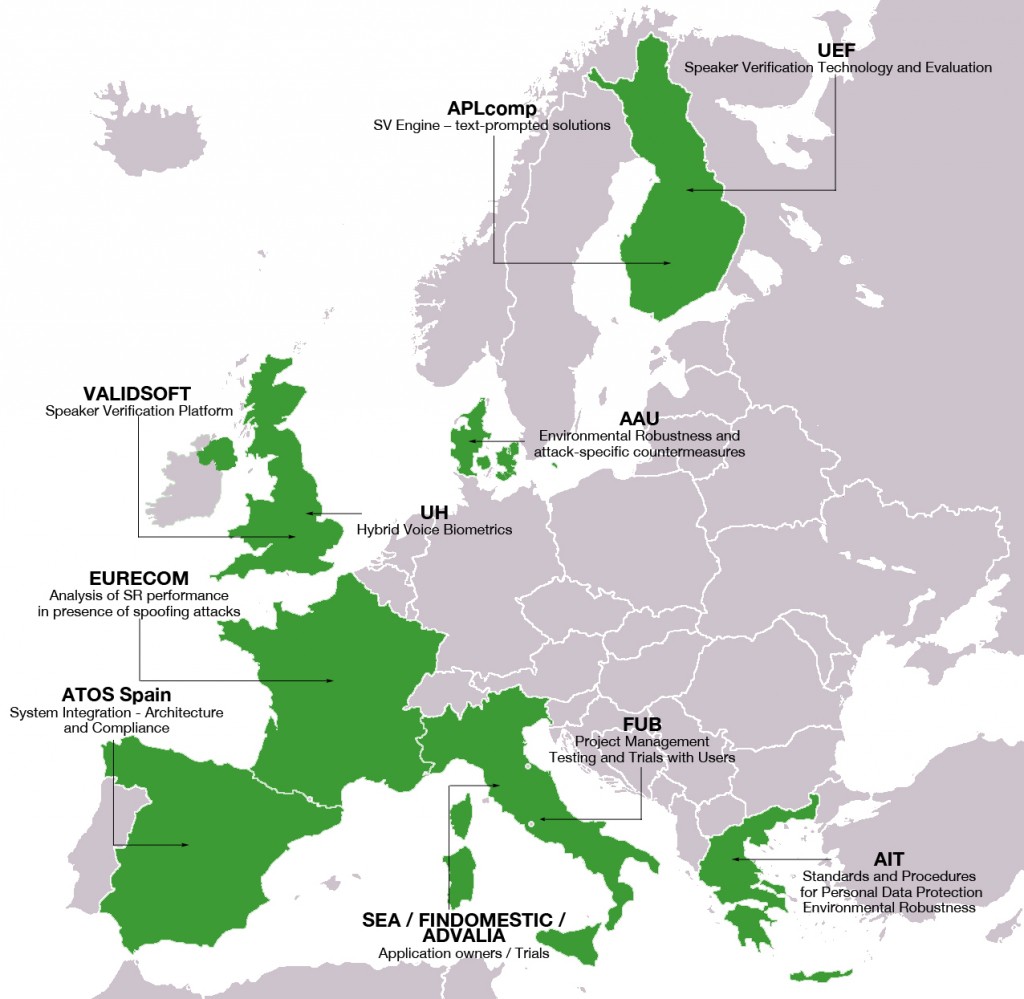
NE: Among our partners, we count Validsoft in the United Kingdom, a voice biometrics product vendor. Eurecom is working with Validsoft to validate Octave technologies in a commercial grade voice biometrics platform. This is not the only category of industrial partners that we work with. Whereas APLcomp are another of Octave’s product vendor partners, Advalia are custom solution developers. ATOS are Octave’s large-scale ICT integrators. Business users are represented by airport operator, SEA, whereas Findomestic, owned by BNP Paribas Personal Finance, represent the banking sector. These two partners, SEA and Findomestic, will help us with evaluation, by offering us the possibility to deploy the TBAS in their respective environments. Airports and banking ecosystems are really different, allowing us to ensure that Octave works in real, diverse conditions.
Learn more about the Octave project
[box type=”shadow” align=”aligncenter” class=”” width=”95%”]
The Octave project:
The Objective Control of Talker Verification (Octave) project is a European project funded through the Horizon 2020 call on “Digital security: cybersecurity, privacy and trust”. It started in June 2015 and will last two years. The research program is segmented in eight work packages, among which the third, “Robustness in speaker verification”, is led by Eurecom. The school, part of the Institut Mines-Télécom, was contacted to work on Octave because of its experience on spoofing detection in voice biometric systems. Previous to Octave, Eurecom was involved in the FP7 project named Tabula Rasa.
List of Octave members:
[/box]




Leave a Reply
Want to join the discussion?Feel free to contribute!